Wazuh Implementation: Homelab Security Made Simple(ish)
Published: 26th May 2025
Alexander Pettersson
Chief Executive Officer
Welcome to our latest tech blog post!
In this post, we will explore our implementation of Wazuh, a powerful open-source security monitoring tool,
that we have integrated into our testing environments. Wazuh provides comprehensive security monitoring,
log analysis, and intrusion detection capabilities, making it a rather useful component in for example your homelab.
I'm not going to go deep into how to install Wazuh and integrate it deeply into your infrastructure,
as that is a very individual and complex task that depends on your specific needs and environment.
Instead, I will provide a high-level overview of an implementation and how you could use Wazuh to enhance your security posture.
Wazuh Architecture
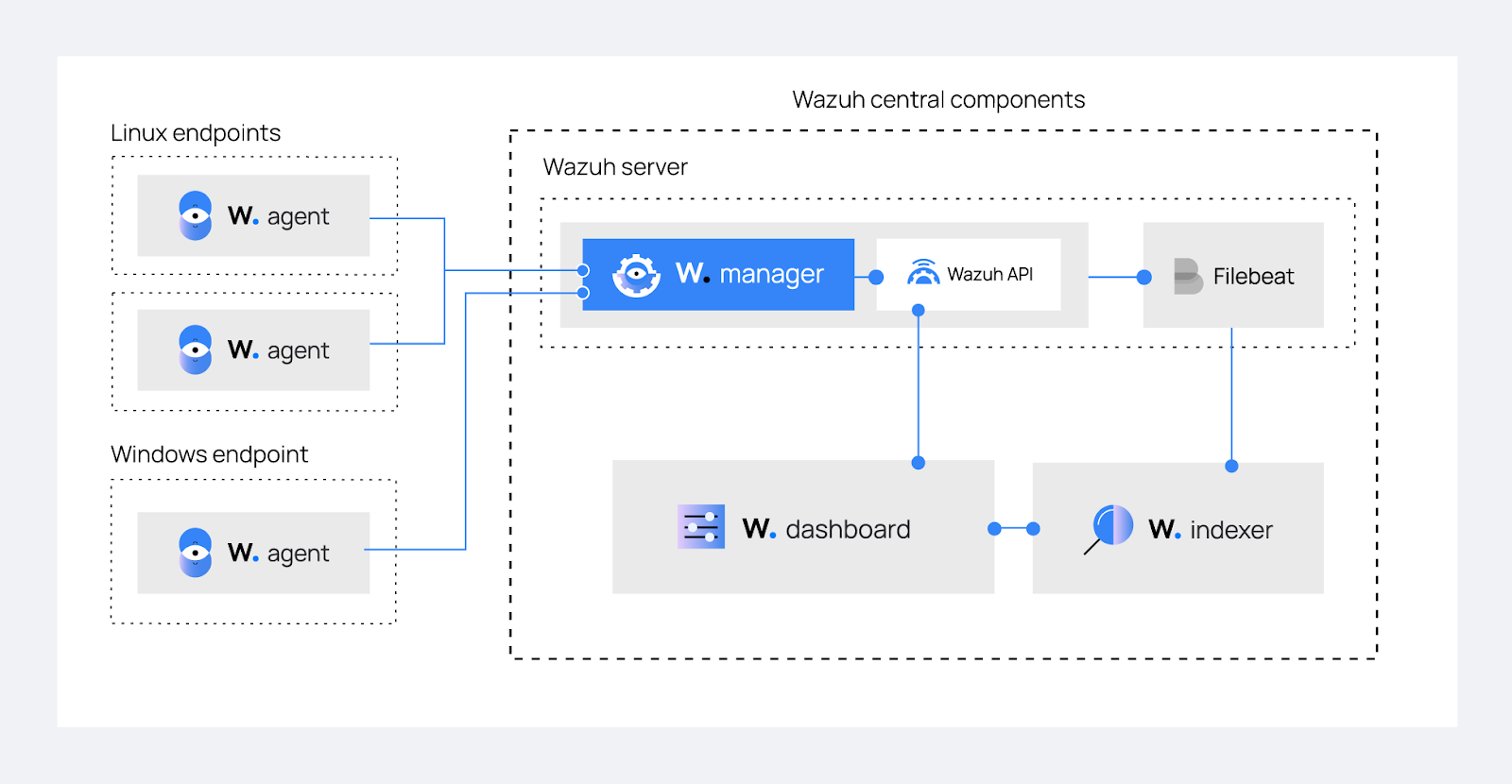
Figure 1: High-level architecture of a Wazuh implementation
The diagram above illustrates the core components of a typical Wazuh implementation. As you can see, Wazuh follows a client-server architecture with agents deployed on monitored systems sending data to a central Wazuh server that processes, analyzes, and indexes the information.
Implementation Details
For our testing environments, we set up Wazuh using Docker, which allows us to easily deploy and manage the Wazuh components. And of course, using docker-compose. We integrated this for testing purposes with our central compose management platform, allowing us to remotely manage the installation without needing to manually SSH into the servers to edit anythingWazuh, of course, supports deployments using various methods, including
• Traditional VM installations,
• Docker or Kubernetes deployments,
• AMIs (Amazon Machine Images),
• Puppet or Ansible
After installing the Wazuh manager, indexer and dashboard, you'll need to configure the agents on the various VMs or containers which you would like to collect information from. These agents can be installed on any system, including
• Linux installations, (of course),
• Windows 10/11 machines,
• MacOS Installations,
PS: Best tip to read more about a PoC installation is in their docs, https://documentation.wazuh.com/current/proof-of-concept-guide/index.html.
Wazuh indexes this data and gives you a powerful web interface to search and analyze the logs. You can set up alerts for specific events, such as failed login attempts, suspicious file changes, or unusual network activity. This allows us to proactively monitor our testing environments and respond to potential security incidents in a timely manner.
PS: If you want to learn more about Wazuh, check out their official documentation at Wazuh Documentation.
Conclusion
In conclusion, Wazuh is a powerful tool for enhancing the security of your infrastructure, whether it's a homelab or a production environment. By implementing Wazuh, you can gain valuable insights into your systems' security posture and can quickly identify and respond to potential threats. But, as with any security tool, it's important to regularly review and update your configurations to ensure that you're getting the most out of Wazuh's capabilities. And it is incredibly important to keep in mind that this system should not be relied on as the sole means of protection for your infrastructure.Keep your APIs safe, and remember sanitation.
Alex, Chief Executive Officer
PS: If you want to learn more about our security practices, check out our policies page.